How to Find the Vulnerability in Small Office Home Office (SOHO) Network

Background
As work-from-home increased since the Covid, securing the small office home office (SOHO) network is quite challenging.
Solution
Firstly, we get the public IP of the network that we would like to test via IPChicken.
Easy Test
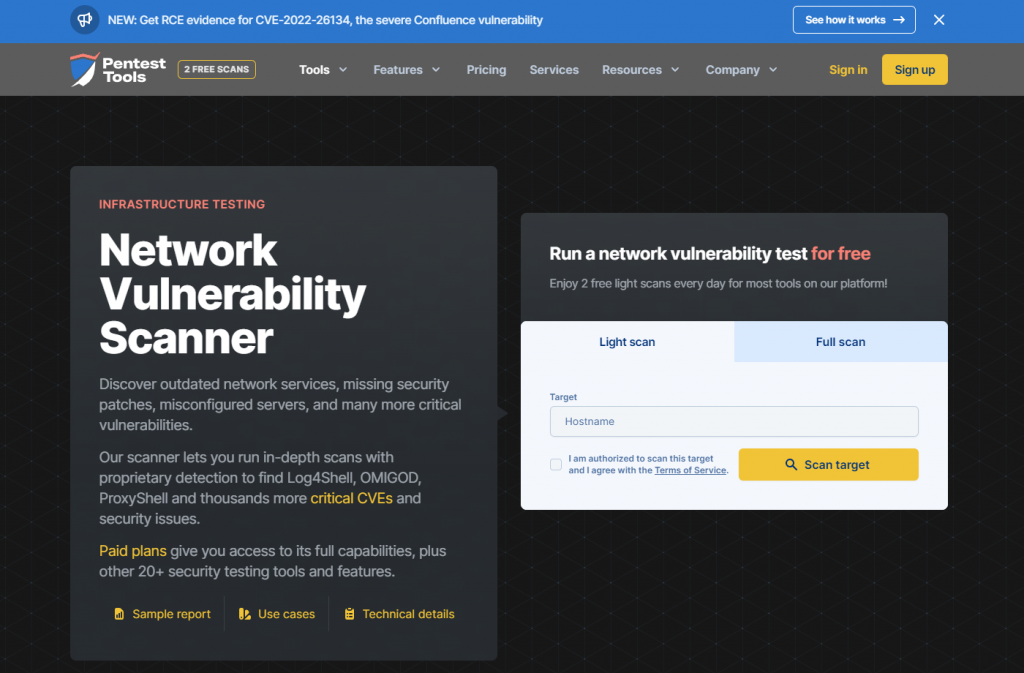
The quick and free solution is to use the tools from PennTest Tool.
On their home page, we click the Scan Your Network option.

We enter the public IP address on the target/hostname and then we click the Scan Target button.
We then review the result.
Advanced Test
We utilise KASM Workspaces on our cloud virtual machine and inside that then we launch the Kali Linux container streaming via any web browser.
If you do not have this environment, you can use an external cloud Linux (Ubuntu) virtual machine and install the Nmap tool.
Note: The hacker used the Nmap to scan the network for vulneravbilities.
To install the nmap tool in Ubuntu, we run the following command:
apt install nmap -yTo test the vulnerability, we run the following command:
nmap -sS -sV -F -D RND:5 [nmap.scanme.org/your_public_ip_address]Response: Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-20 02:48 UTC Nmap scan report for X.X.X.X. Host is up (0.31s latency). All 1000 scanned ports on X.X.X.X are in ignored states. Not shown: 1000 filtered tcp ports (no-response) To do the advanced test with vulnerability, we run another command:
nmap --script vuln -D RND:5 [nmap.scanme.org/your_public_ip_address]Notes
The excellent “Nmap Network Discovery” book, written by its creator Fyodor explains this very well. We quote filtered : Nmap cannot determine whether the port is open because packet filtering prevents its probes from reaching the port. The filtering could be from a dedicated firewall device, router rules, or host-based firewall software. These ports frustrate attackers because they provide so little information. Sometimes they respond with ICMP error messages such as type 3 code 13 (destination unreachable: communication administratively prohibited), but filters that simply drop probes without responding are far more common. This forces Nmap to retry several times just in case the probe was dropped due to network congestion rather than filtering. This sort of filtering slows scans down dramatically.
open|filtered : Nmap places ports in this state when it is unable to determine whether a port is open or filtered. This occurs for scan types in which open ports give no response. The lack of response could also mean that a packet filter dropped the probe or any response it elicited. So Nmap does not know for sure whether the port is open or being filtered. The UDP, IP protocol, FIN, NULL, and Xmas scans classify ports this way.
closed|filtered : This state is used when Nmap is unable to determine whether a port is closed or filtered. It is only used for the IP ID Idle scan discussed in Section 5.10, “TCP Idle Scan (-sl)
Source: https://unix.stackexchange.com/questions/136683/why-are-some-ports-reported-by-nmap-filtered-and-not-the-others
What From Here
Once we find the vulnerability, we make a note of the findings. Go to the router to change the configuration as necessary.
We suggest following this blog post on how to harden the router for the home office in 2022.
The End
Congratulation on reaching the end of this article! We hope that we have been able to shed some light on how to find the vulnerability in your small office home office (SOHO) network.
We write this in such a way that this is not a fixed article. Like in this journey, we learn as we go and we re-write some parts of the article so please keep pinging with this article or any general tech posts.
We also would love to hear about how you deal with the situation and what IT-related challenges you might be facing. Please feel free to leave us a comment below this article or you can contact us on the Dewacorp website for your IT support, application integration, application development, or other IT-related. Alternatively, you can casually have a chat on Dewachat. Let us know if you have any questions that we can help with!
Big thank you for the photo by Tima Miroshnichenko on Pexels.
If you want to boost your product and service to the wider web community, you can visit our Dewalist classified website – home to 31,000+ active users and 40,000+ active advertising so far. Check it out!
If you love this security article or any security posts and you would like to receive an update of this article or our latest post, please sign up for the form below:









